Check Snmp Version Windows
For checking SNMP in Windows OS Go to Start- Settings- Control Panel-Administrative Tools- Services Check for SNMP Service. If SNMP Service does not exist, install SNMP. Because of security issues with any version prior to SNMP v3, our servers get flagged and it's something that we need to fix. So, having said all that, does Windows Server 2016 support SNMPv3. Oh, and I also installed Windows Server 2016 in my test environment and SNMP is still available.
Applies to: Windows Server 2022, Windows 10, Windows 8.1, Windows 8, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
This article describes how to enable and disable Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3) on the SMB client and server components.
While disabling or removing SMBv1 might cause some compatibility issues with old computers or software, SMBv1 has significant security vulnerabilities and we strongly encourage you not to use it.
Disabling SMBv2 or SMBv3 for troubleshooting
We recommend keeping SMBv2 and SMBv3 enabled, but you might find it useful to disable one temporarily for troubleshooting. For more information, see How to detect status, enable, and disable SMB protocols on the SMB Server.
In Windows 10, Windows 8.1, and Windows 8, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, and Windows Server 2012, disabling SMBv3 deactivates the following functionality:
- Transparent Failover - clients reconnect without interruption to cluster nodes during maintenance or failover
- Scale Out - concurrent access to shared data on all file cluster nodes
- Multichannel - aggregation of network bandwidth and fault tolerance if multiple paths are available between client and server
- SMB Direct - adds RDMA networking support for high performance, with low latency and low CPU use
- Encryption - Provides end-to-end encryption and protects from eavesdropping on untrustworthy networks
- Directory Leasing - Improves application response times in branch offices through caching
- Performance Optimizations - optimizations for small random read/write I/O
In Windows 7 and Windows Server 2008 R2, disabling SMBv2 deactivates the following functionality:
- Request compounding - allows for sending multiple SMBv2 requests as a single network request
- Larger reads and writes - better use of faster networks
- Caching of folder and file properties - clients keep local copies of folders and files
- Durable handles - allow for connection to transparently reconnect to the server if there's a temporary disconnection
- Improved message signing - HMAC SHA-256 replaces MD5 as hashing algorithm
- Improved scalability for file sharing - number of users, shares, and open files per server greatly increased
- Support for symbolic links
- Client oplock leasing model - limits the data transferred between the client and server, improving performance on high-latency networks and increasing SMB server scalability
- Large MTU support - for full use of 10 Gigabit Ethernet (GbE)
- Improved energy efficiency - clients that have open files to a server can sleep
The SMBv2 protocol was introduced in Windows Vista and Windows Server 2008, while the SMBv3 protocol was introduced in Windows 8 and Windows Server 2012. For more information about SMBv2 and SMBv3 capabilities, see the following articles:
How to remove SMBv1

Motogp 3 urt fix. Here's how to remove SMBv1 in Windows 10, Windows 8.1, Windows Server 2019, Windows Server 2016, and Windows 2012 R2.
PowerShell methods
SMBv1 (client and server)
Detect:
Disable:
Enable:
Windows Server 2012 R2, Windows Server 2016, Windows Server 2019: Server Manager method for disabling SMB
SMBv1
To remove SMBv1 from Windows Server:
- On the Server Manager Dashboard of the server where you want to remove SMBv1, under Configure this local server, select Add roles and features.
- On the Before you begin page, select Start the Remove Roles and Features Wizard, and then on the following page, select Next.
- On the Select destination server page under Server Pool, ensure that the server you want to remove the feature from is selected, and then select Next.
- On the Remove server roles page, select Next.
- On the Remove features page, clear the check box for SMB 1.0/CIFS File Sharing Support and select Next.
- On the Confirm removal selections page, confirm that the feature is listed, and then select Remove.
Windows 8.1 and Windows 10: PowerShell method
SMBv1 Protocol
Detect:
Disable:
Enable:
SMBv2/v3 Protocol (only disables SMBv2/v3 Server)
Detect:
Disable:
Enable:
Windows 8.1 and Windows 10: Add or Remove Programs method
To disable SMBv1 on Windows 8.1 and Windows 10:
- In Control Panel, select Programs and Features.
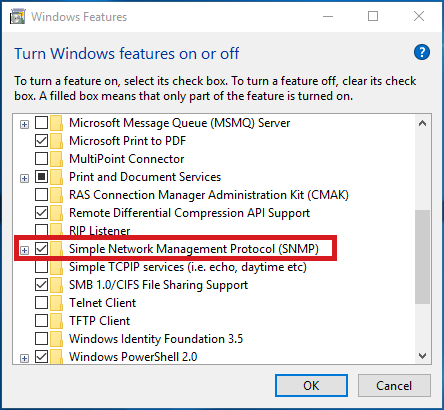
- Under Control Panel Home, select Turn Windows features on or off to open the Windows Features box.
- In the Windows Features box, scroll down the list, clear the check box for SMB 1.0/CIFS File Sharing Support and select OK.
- After Windows applies the change, on the confirmation page, select Restart now.
How to detect status, enable, and disable SMB protocols on the SMB Server
For Windows 8 and Windows Server 2012
Windows 8 and Windows Server 2012 introduced the new Set-SMBServerConfiguration Windows PowerShell cmdlet. The cmdlet enables you to enable or disable the SMBv1, SMBv2, and SMBv3 protocols on the server component.
Note
When you enable or disable SMBv2 in Windows 8 or Windows Server 2012, SMBv3 is also enabled or disabled. This behavior occurs because these protocols share the same stack.
You don't have to restart the computer after you run the Set-SMBServerConfiguration cmdlet.
SMBv1 on SMB Server
Detect:
Disable:
Enable: Big fish audio trapture trap and hip hop kontakt download free.
For more information, see Server storage at Microsoft.
SMB v2/v3 on SMB Server
Detect:
Disable:
Enable:
For Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008
To enable or disable SMB protocols on an SMB Server that is running Windows 7, Windows Server 2008 R2, Windows Vista, or Windows Server 2008, use Windows PowerShell or Registry Editor.
PowerShell methods
Note
This method requires PowerShell 2.0 or later version of PowerShell.
SMBv1 on SMB Server
Detect:
Default configuration = Enabled (No registry key is created), so no SMB1 value will be returned
Disable:
Enable:
Note You must restart the computer after you make these changes.For more information, see Server storage at Microsoft.
SMBv2/v3 on SMB Server
Detect:
Disable:
Enable:
Note
You must restart the computer after you make these changes.
Registry Editor
Important
Follow the steps in this section carefully. Serious problems might occur if you modify the registry incorrectly. Before you modify it, back up the registry for restoration in case problems occur.
To enable or disable SMBv1 on the SMB server, configure the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters

To enable or disable SMBv2 on the SMB server, configure the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
Note
You must restart the computer after you make these changes.
How to detect status, enable, and disable SMB protocols on the SMB Client
For Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, and Windows Server 2012
Note
When you enable or disable SMBv2 in Windows 8 or in Windows Server 2012, SMBv3 is also enabled or disabled. This behavior occurs because these protocols share the same stack.
SMBv1 on SMB Client
Detect
Disable:
Enable:
For more information, see Server storage at Microsoft
SMBv2/v3 on SMB Client
Detect:
Disable:
Enable:
Check Windows Server Snmp Version
Note
- You must run these commands at an elevated command prompt.
- You must restart the computer after you make these changes.
Disable SMBv1 Server with Group Policy
This procedure configures the following new item in the registry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
- Registry entry: SMB1
- REG_DWORD: 0 = Disabled
To use Group Policy to configure this, follow these steps:
Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit.
In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
Right-click the Registry node, point to New, and select Registry Item.
In the New Registry Properties dialog box, select the following:
- Action: Create
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEMCurrentControlSetServicesLanmanServerParameters
- Value name: SMB1
- Value type: REG_DWORD
- Value data: 0
This procedure disables the SMBv1 Server components. This Group Policy must be applied to all necessary workstations, servers, and domain controllers in the domain.
Note
WMI filters can also be set to exclude unsupported operating systems or selected exclusions, such as Windows XP.
Important
Be careful when you make these changes on domain controllers on which legacy Windows XP or older Linux and third-party systems (that don't support SMBv2 or SMBv3) require access to SYSVOL or other file shares where SMB v1 is being disabled.
Disable SMBv1 Client with Group Policy
To disable the SMBv1 client, the services registry key needs to be updated to disable the start of MRxSMB10 and then the dependency on MRxSMB10 needs to be removed from the entry for LanmanWorkstation so that it can start normally without requiring MRxSMB10 to first start.
This guidance updates and replaces the default values in the following two items in the registry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesmrxsmb10
Registry entry: Start REG_DWORD: 4= Disabled
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanWorkstation
Registry entry: DependOnService REG_MULTI_SZ: 'Bowser','MRxSmb20″,'NSI'
Note
The default included MRxSMB10 which is now removed as dependency.
To configure this by using Group Policy, follow these steps:
Open the Group Policy Management Console. Right-click the GPO that should contain the new preference item, and then click Edit.
In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
Right-click the Registry node, point to New, and select Registry Item.
In the New Registry Properties dialog box, select the following:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEMCurrentControlSetservicesmrxsmb10
- Value name: Start
- Value type: REG_DWORD
- Value data: 4
Then remove the dependency on the MRxSMB10 that was disabled.
In the New Registry Properties dialog box, select the following:
- Action: Replace
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEMCurrentControlSetServicesLanmanWorkstation
- Value name: DependOnService
- Value type: REG_MULTI_SZ
- Value data:
- Bowser
- MRxSmb20
- NSI
Note
These three strings will not have bullets (see the following screen shot).
The default value includes MRxSMB10 in many versions of Windows, so by replacing them with this multi-value string, it is in effect removing MRxSMB10 as a dependency for LanmanServer and going from four default values down to just these three values above.
Note
When you use Group Policy Management Console, you don't have to use quotation marks or commas. Just type each entry on individual lines.
Restart the targeted systems to finish disabling SMB v1.
Auditing SMBv1 usage
To determine which clients are attempting to connect to an SMB server with SMBv1, you can enable auditing on Windows Server 2016, Windows 10, and Windows Server 2019. You can also audit on Windows 7 and Windows Server 2008 R2 if the May 2018 monthly update is installed, and on Windows 8.1 and Windows Server 2012 R2 if the July 2017 monthly update is installed.
Enable:
Disable:
Detect:
When SMBv1 auditing is enabled, event 3000 appears in the 'Microsoft-Windows-SMBServerAudit' event log, identifying each client that attempts to connect with SMBv1.
Summary
If all the settings are in the same GPO, Group Policy Management displays the following settings.
Testing and validation
After completing the configuration steps in this article, allow the policy to replicate and update. As necessary for testing, run gpupdate /force at a command prompt, and then review the target computers to make sure that the registry settings are applied correctly. Make sure SMBv2 and SMBv3 are functioning for all other systems in the environment.
-->[SNMP is available for use in the operating systems specified in the Requirements section. It may be altered or unavailable in subsequent versions. Instead, use Windows Remote Management, which is the Microsoft implementation of WS-Man.]
Purpose
The Microsoft Windows implementation of the Simple Network Management Protocol (SNMP) is used to configure remote devices, monitor network performance, audit network usage, and detect network faults or inappropriate access.
Important
The Microsoft Windows SNMP API only supports protocol versions up to SNMPv2C. It does not support any later versions of the protocol.
Where applicable
SNMP uses a distributed architecture consisting of management applications and agent applications. The SNMP service implements an SNMP agent. To use the information the SNMP service provides, you must have at least one host that is running an SNMP management application. You can use third-party SNMP management software, or you can develop your own SNMP management software application. The following APIs are available for this purpose:
- SNMP Management API, a set of functions that can be used to quickly develop basic SNMP management systems
- WinSNMP API, version 2.0, a set of functions for encoding, decoding, sending, and receiving SNMP messages
Additionally, the SNMP Extension Agent API defines the interface between the SNMP service and third-party SNMP extension agent DLLs. The SNMP Utility API functions can be used to simplify the processing of SNMP messages.
Developer audience
The APIs listed in the preceding section are designed for use by C/C++ programmers. Familiarity with SNMP and SNMPv2C, as well as a working knowledge of networking and network management concepts, are required.
Run-time requirements
For more information about the operating system required to use a particular function, see the Requirements section of the reference page for that function.
In this section
| Topic | Description |
|---|---|
| New in SNMP | Information on updates to SNMP. |
| Simple Network Management Protocol (SNMP) | Information and API reference for SNMP, including the SNMP Management API, SNMP Extension Agent API, and SNMP Utility API functions. |
| WinSNMP API | Information and API reference for the Microsoft Windows SNMP Application Programming Interface (WinSNMP API). |